Antivirus 2009
Analysis of a fake antivirus scam
Overview:
This article describes an investigation into the cause of infection of AntiSpyware2009 and similar malware.
Goals:
- Find where this malware lives
- Find how this malware is installed
Method:
This research was performed on two VMWare Server 2 virtual machines, on an Internet connected computer, isolated by a firewall from any other computers on the site.
The two computers were:
- Windows 2000, Service Pack 4, Internet explorer 6 and Firefox 3, All windows updates installed
- Windows XP, Service Pack 3, no updates installed. Internet Explorer 6 and 7 tested.
Online research provided the researcher with several possible malicious websites. These sites were opened in the web browsers of the test machines.
Results:
The virus was discovered on several servers designed to handle redirects from other sites. These redirects come from sites that have been tampered with, usually by installing a .htaccess file that redirects users who visit an otherwise legitimate site.
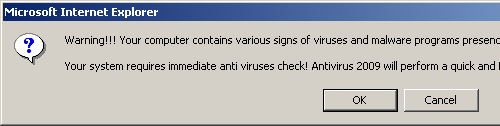
Two different sites were found containing this virus. Each site presented several “warning” dialog boxes, telling the user they had a virus, and needed to run Antivirus 2009. Two examples of this dialogue are shown:
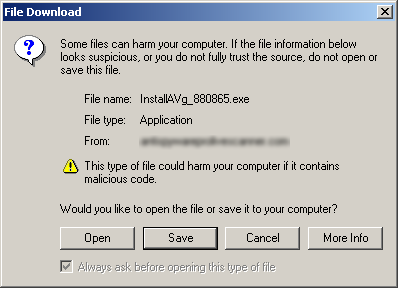
- These dialog boxes show “Microsoft Internet Explorer” in the blue title bar. This is a limitation of the scam. A true virus scanner running on your system would be able to present an appropriate title bar, representing the correct name or function of the software. Seeing the name of your web-browser in the title bar is a give-away that the message is being generated by a web page inside the browser, and not by software on your system.
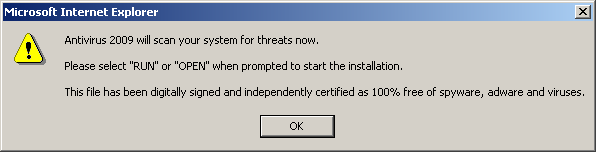
The site then presents a mock virus scan, which quickly pretends to find several (hundred) infections. Clicking on any part of the page at any time causes a file download dialog to show, allowing the user to download and install the malware on their system.
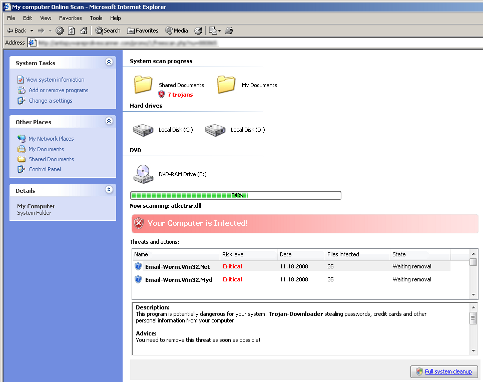
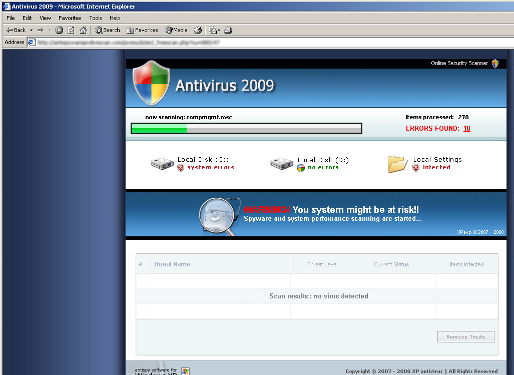
- Again, in both these examples, the falsified scan is bounded within the Internet Explorer window, and Internet Explores title-bar, menu and controls are visible at the top of the falsified scan. Furthermore, minimising the Internet Explorers window also hides the scan within it (This is not a foolproof test)
- The scans claim to be scanning a C:\ drive and a D:\ drive, both hard drives. I know that my system only had one hard disk drive, so this report is clearly false.
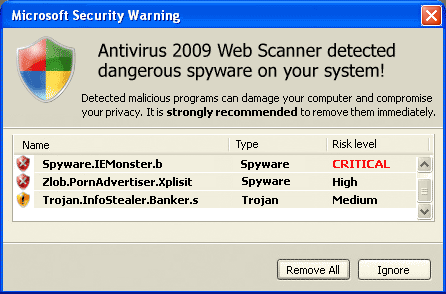
On completion of the falsified scan, the scam presents a warning that viruses have been found and should be removed. These warnings are simply images shown within the browser, allowing them to look very realistic.
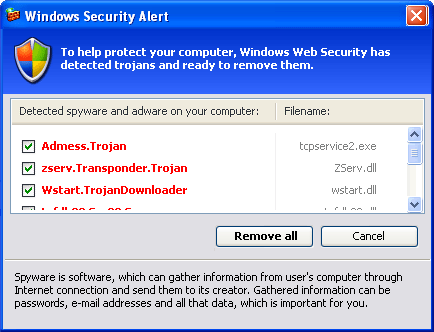
- Again, these screens are contained within the browser. Closing or moving the browser also moves these windows.
- Being a static image, these do not react the way normal windows do. The mouse cursor is incorrect over much of the image, normal windows hover highlighting does not work.
Clicking on any part of the browser frame causes a file download window to appear. Curiously it always seems to have the letters “AVg”, possibly to make the user think its the common Grisoft AVG virus scanner. Running this file will install the Antivirus 2009 malware package on the computer.
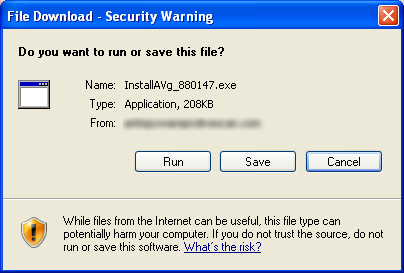
- An important principal in computer security is not to accept files from someone you don’t know. Though this may appear to be a legitimate virus scanner, nowhere is the following information available:
- The name of the software vendor
- The location of the software vendor
- The vendors website or other contact details
- Any other information about the software, the license (describing who is allowed to use it, and for what purposes), and if the software is a trial or fully functioning.
This research did not proceed to install the malware and observe its behaviours, the goals were only to discover how infection occurred.
The files however were analysed, and were found to be viruses, both similar variants. Unfortunately only a few virus scanners actually detected this. The reason is unknown. Perhaps the virus is some form of self-modifying virus, which some scanners have difficulty detecting.
At the time of analysis (24th Jan), only three virus scanners were known to detect any virus in these files. Now a week later, 15-25 virus scanners (40-60%) now see it. Unfortunately, a newly downloaded file (recently updated by the virus writer) is only detected by 5 scanners. It seems the authors are constantly publishing new versions to hinder detection by virus scanners. (1 2 3)
Conclusion:
It was suspected before investigation that infection was due to a browser exploit, allowing the virus to install itself without user knowledge or consent. This was not found to be the case, rather, the user must knowingly install the virus, presumably after being convinced by the false virus report that it is a desirable course of action. Thus infection from these sites is preventable with user training.
Recommendations to users to avoid this style of attack are as follows.
- Know what virus scanners and security software are installed on your computer. If you see anything unfamiliar when using the Internet, be suspicious.
- Know what this software is called, and what it looks like.
- Other common security software you may not be aware of is Windows Defender and Microsoft Malicious Software Removal Tool.
- Before downloading any file from the Internet or email;
- Know that running a file potentially allows it full access to your system, to modify it in any way, and use whatever techniques it has available to hide any virus activity.
- Know and trust the author of the file. Ensure you are receiving the file directly from the author, so that you are sure the file has not been tampered with.
- Always browse the Internet with an up-to-date browser. In this testing, Firefox 3 prevented me from visiting these sites, warning that they were known to contain malwarre.
- Avoid browsing with older or unsupported operating systems.
- Ensure all your system software is kept up to date, Turn on Microsoft Update or Windows Update in Windows.